Deploying Smoothwall Express 3.1 (Explicit Proxy)
Smoothwall Express is a open source project setup in year 2000 to develop a free firewall that includes its own security-hardened GNU/Linux operating system and easy to use web interface.
This product is not to be mistaken for the commercial corporate product “smoothwall” which is a a very powerful web filtering and security appliance that can be used to control web traffic in depth working up to layer 7 of the OSI model.
The smoothwall express device can deployed in two methods,
Explicit Mode: In explicit mode, requests are sent to the proxy device for analysis and matching from hosts as the traffic travels from inside to the outside network, using this method means users would need to define a proxy server inside their internet options. The proxy server can also be bypassed if the settings are removed from internet options and the firewall is allowing hosts to get out on http and https.
Transparent Mode: In transparent mode, the data must pass the device in order to get out, its like a bump in the wire, this method is more secure in the sense that requests are not sent to the proxy server however the proxy server is the ultimate destination. No settings need to be defined inside internet options when using this method.
Smoothwall Express is a great free product, however there are limitations – these include the lack of NAT and VLAN support. Currently only one network per interface may be defined, so if you have multiple VLANs it will be tricky to get them all to work. Regardless of the limitations this is a good product and was designed for home use, however small business can take advantages too.
In this step by step guide we will go through the process of deploying smoothwall express as a VM in Hyper-V and configuring the device with basic settings to act as a explicit proxy.
Although Im using Hyper-V the device can also be deployed using VMware ESXI/WS Oracale VB
Below is the topology that we will be working with:
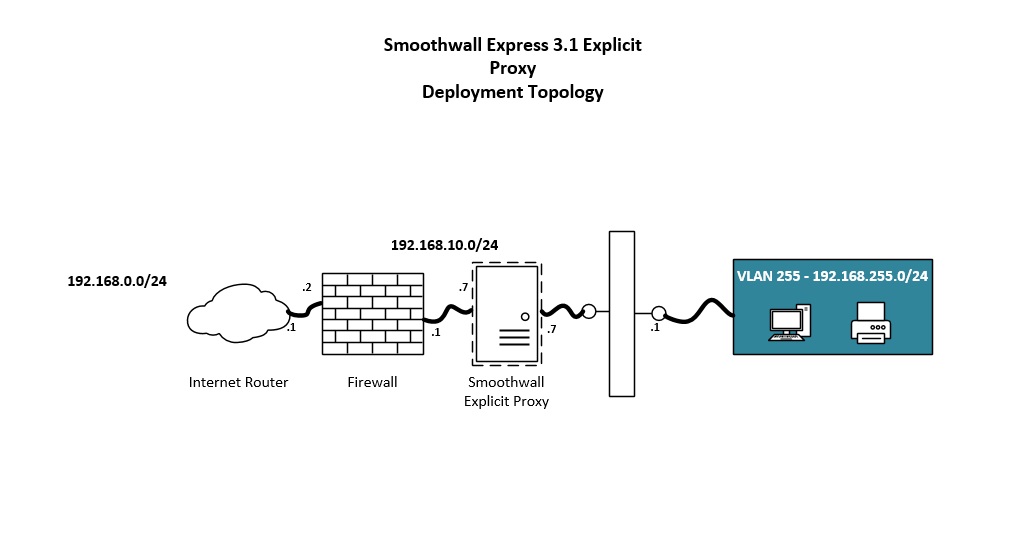
Lets get started!
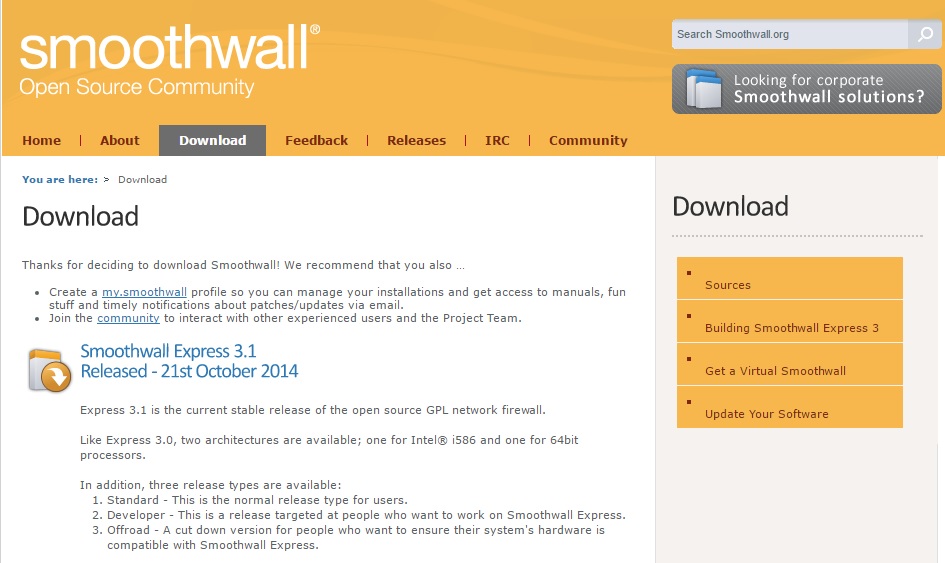
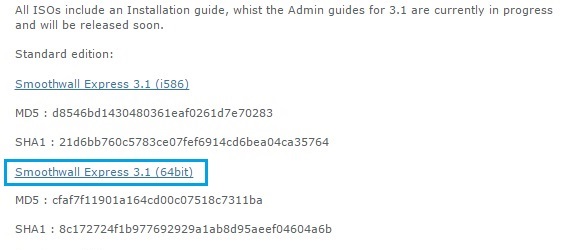
1. Download “smoothwall express 3.1” from www.smoothwall.org , you have the option to download a standard/developer/offroad version in 32bit or 63bit, in this example we will use the standard 64bit version. There is also a .OVA template of V3.0 for ESXI if that’s your preferred flavor.
2. Launch “Hyper V”, right click the host and click “New” – “Virtual Machine”
3. At the wizard, click “Next”
4. Give the virtual machine a name and specify a location to store the VM, click “Next”
5. In order for the device to be able to boot using an IDE controller and run the version of OS we require, we must use a Gen 1 VM, Select “Generation 1” click “Next”
6. Allocate memory for the VM, in this case i have allocated “2048”, you can allocate a smaller amount if you do not have enough RAM. Click “Next”
7. By default the VM will have a single NIC, connect the default NIC to the virtual switch for network connectivity. Click “Next”
8. Create a new had drive and allocate 50GB as its size, specify a location to store the VHD file and click “Next”
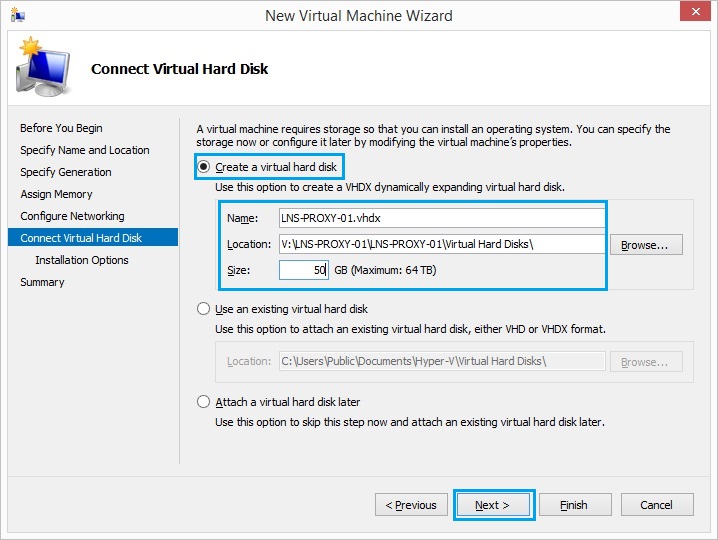
9. Select “Install an operating system from a bootable CD/DVD-ROM” and select “Image file (ISO)” browse for the “Smoothwall Express 3.1” ISO downloaded earlier. Click “Next”
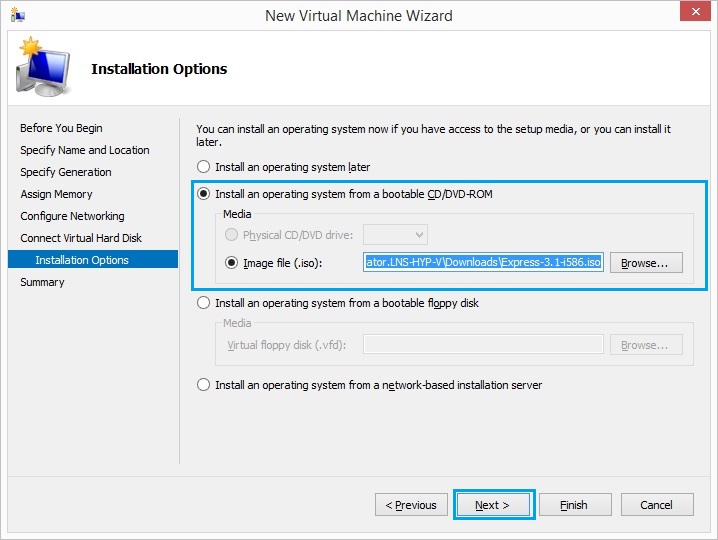
10. Review the information on the window and click “Finish”
Hyper-V will create the VM
11. Now that the VM has been created we need to edit the settings to add an additional NIC, right click the VM and select “Settings”
12. From the left hand pane select “Add Hardware” and select “Network Adapter”, click “Add”
13. Select the newly created NIC from the left pane, and allocate to the virtual switch
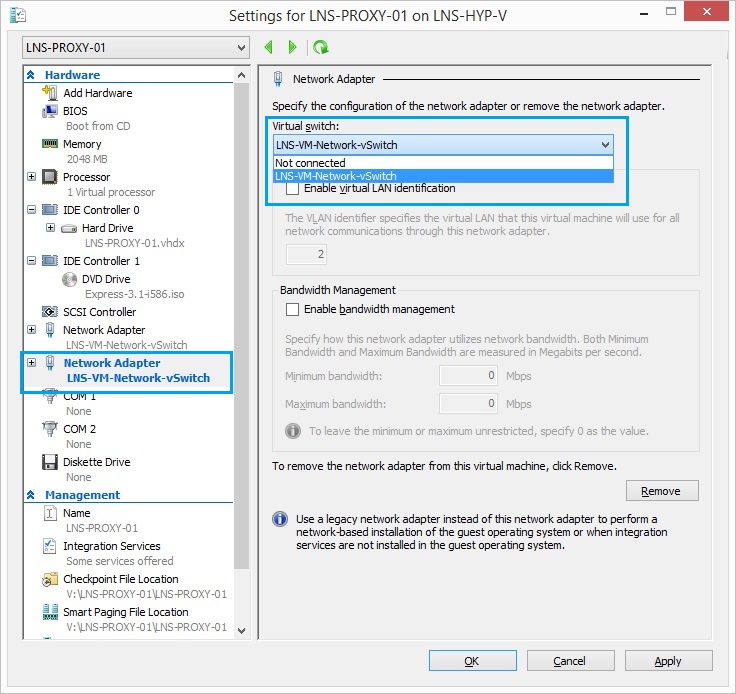
14. Still under the new NIC, tick “VLAN ID” and specify the VLAN that will be used for the outside interface of the smoothwall device, this interface will connect to the firewall or WAN router.
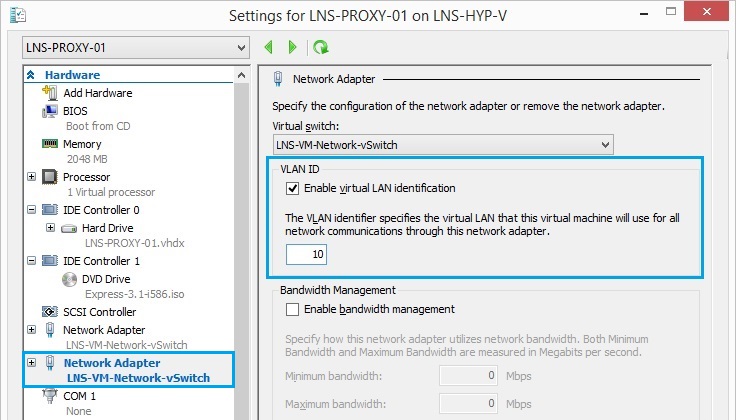
15. Now select the default NIC that was created as part of the VM creation and amend the VLAN settings. This will be for the inside part of the network where the requests will be sent to the smoothwall proxy from inside hosts. in this example Im using VLAN 255.
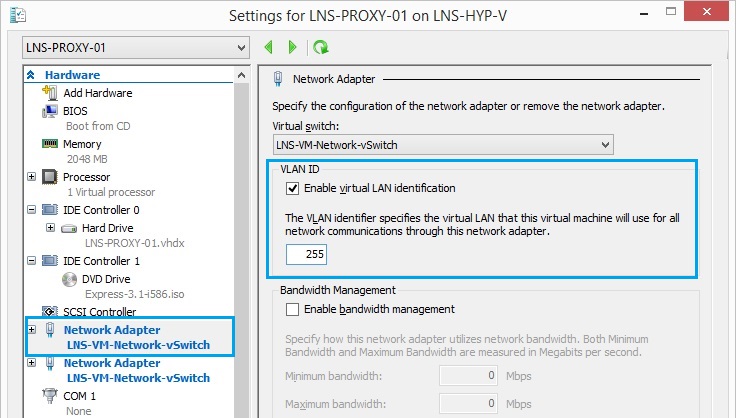
16. Click “Apply” and hit “OK” to save and close the settings window
17. Right click the VM and select “Connect”
18. The console window will appear, hit the “Start” button to fire up the VM
19. the VM will boot the ISO previously loaded, select “Install Smoothwall Express”
20. Click “OK” at the notice
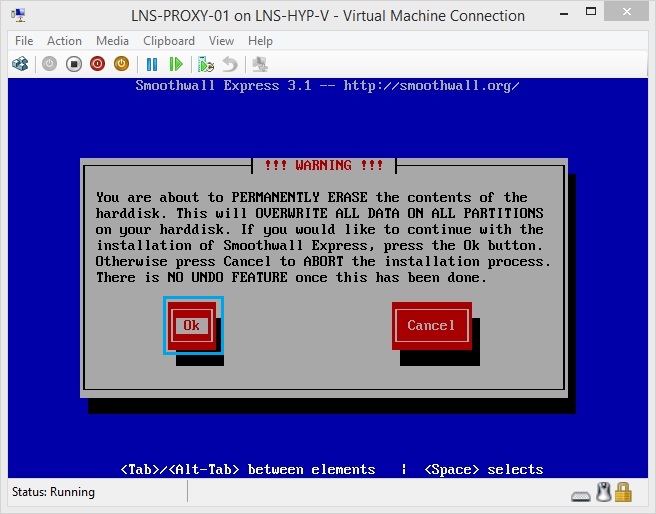
21. Click “OK” to allow the installation to format and partition the hard disk.
22. Click “OK” at the format warning
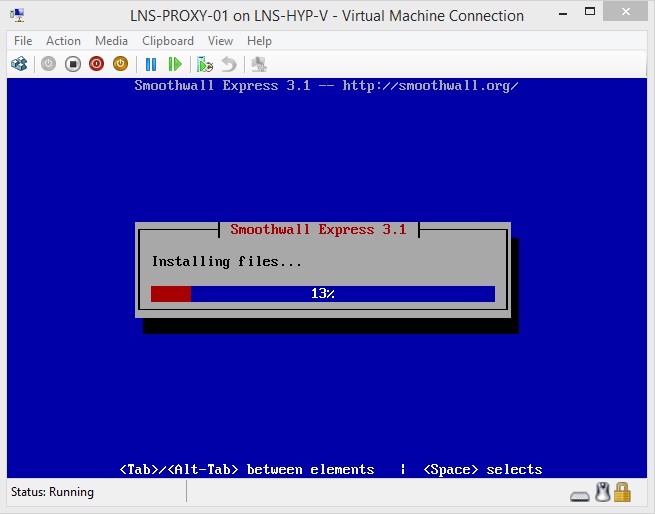
The installation of the files will begin
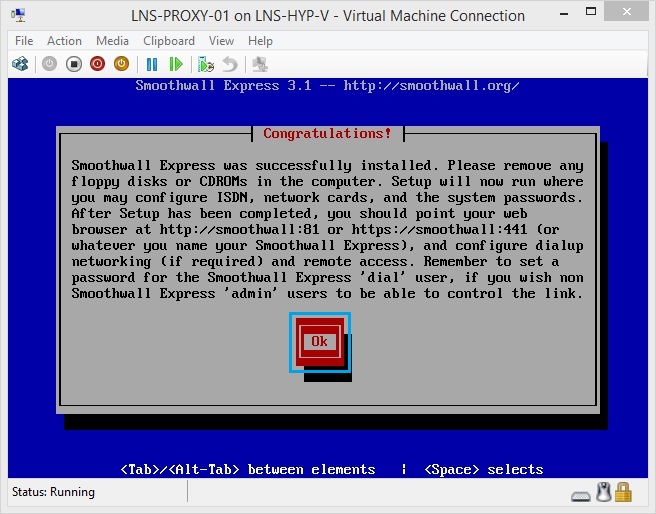
23. At the message “Smoothwall Express was successfully Installed” click “OK”
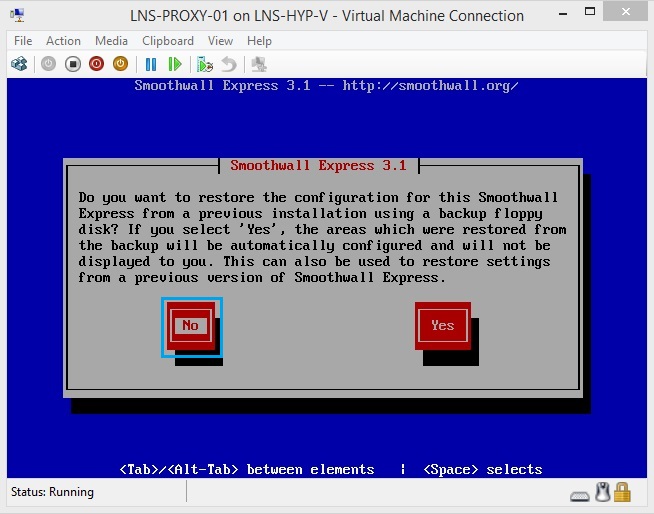
24. At the message below click “NO”
25. Select “UK” and click “OK”
26. Select the correct timezone and click “OK”
27. Give the device a hostname and click “OK”, in this case i have left it as “smoothwall”
28. At this stage you can select what type of security policy you would like to implement on outgoing traffic, you can leave all outgoing traffic as open/half-open or closed, the default is “half-open” which i have selected for this example. you can also amend this later.
29. At the next window select “Network configuration type” and click “OK”
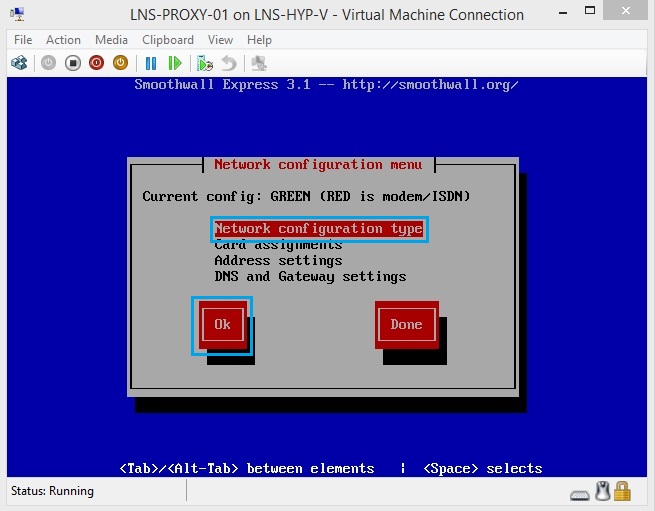
30. This menu allows you to select the interfaces that you want to use in the deployment – in other terms these are like zones which is represented by a color. “Green + Red” for two zones such as Inside and Outside, or “Green + Orange + Red” for 3 zones such as Inside, DMZ, Outside. For our deployment we will need two zones, Select “Green + Red” and hit “OK”
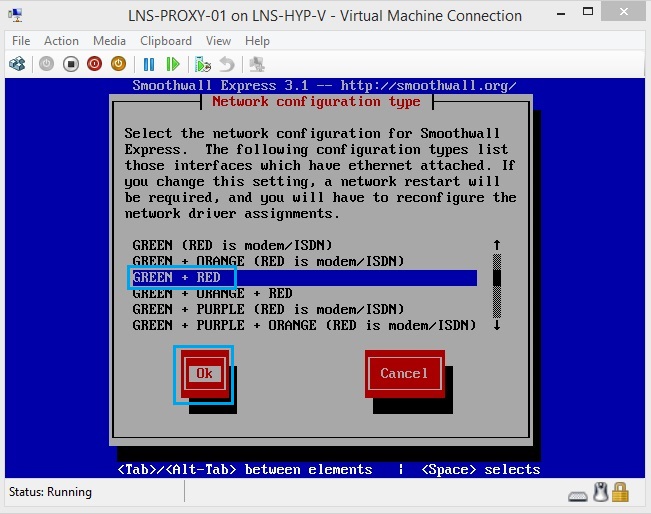
31. Select “card assignments” and click “OK”
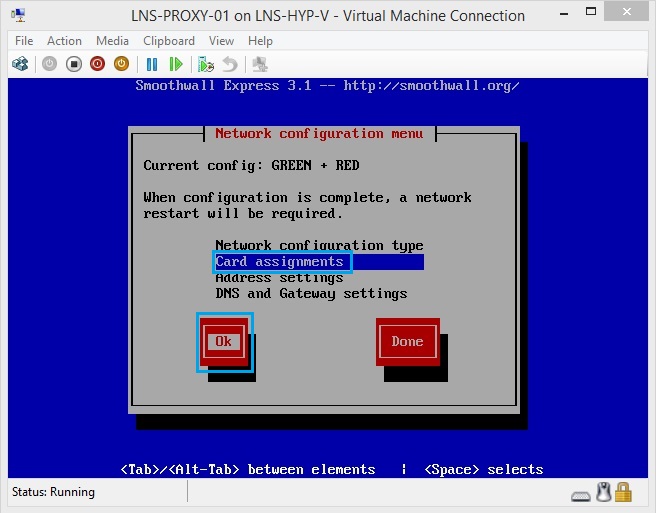
32. From this menu we will assign a NIC to a zone, click “OK” to proceed
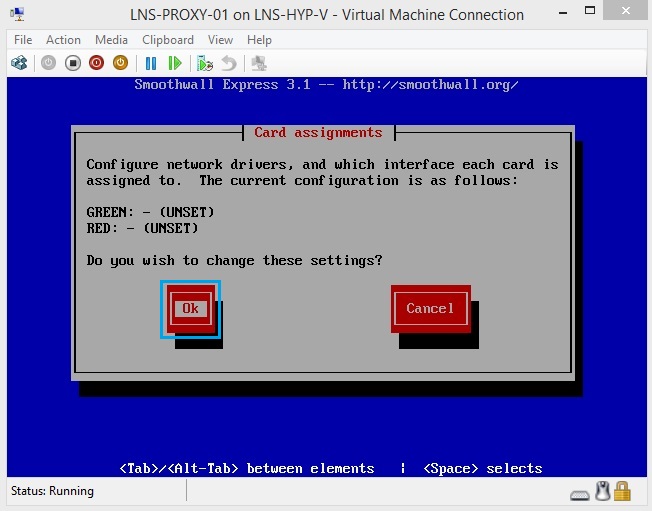
33. From the first NIC select “Green” and hit “OK”(make sure the MAC address matches the VM NIC allocated to VLAN 255) this will be the “Inside” zone
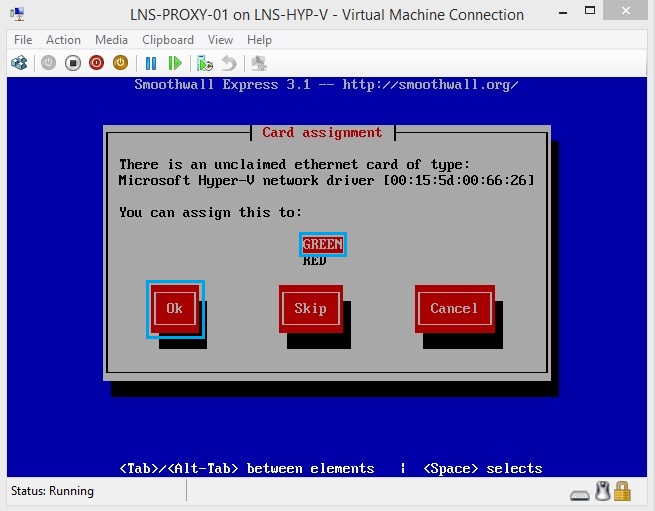
34. Now for the second NIC select “Red” and hit “OK” this will be our “Outside” Zone
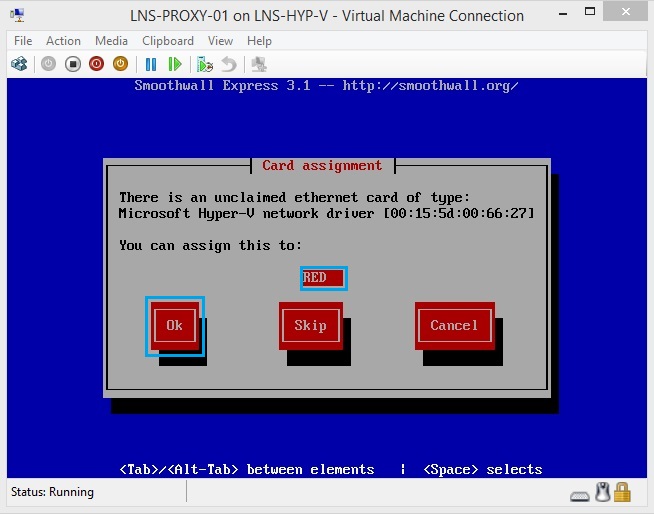
35. Once all card have been successfully allocated click “OK”
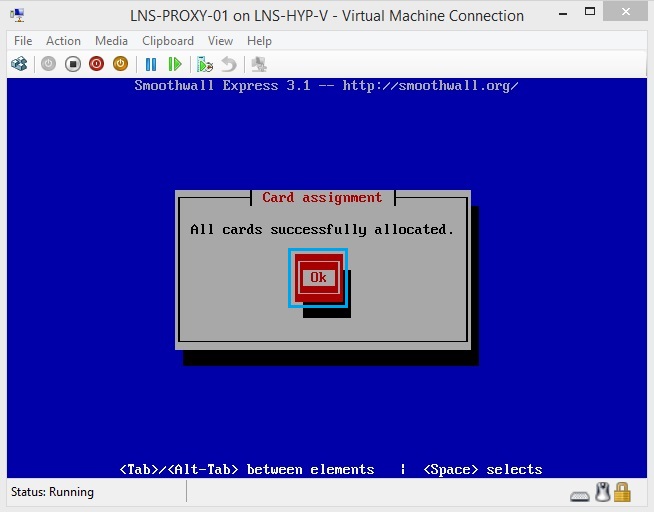
36. Select “Address settings” and hit “OK”
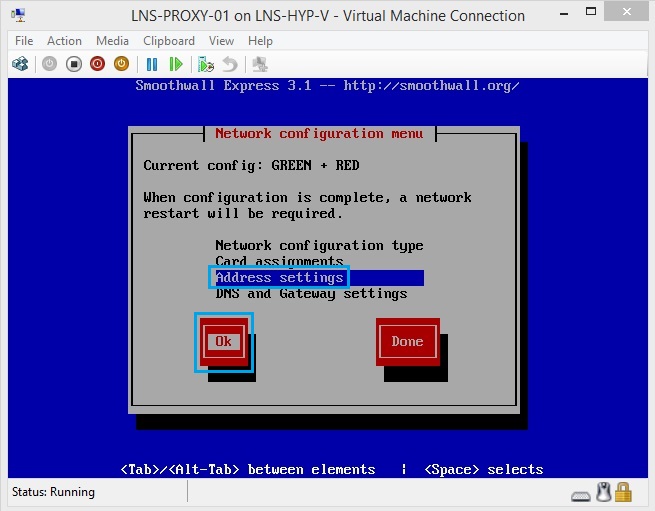
37. Select “Green” and hit “OK” to specify IP details for the Inside zone.
38. Click “OK” to proceed
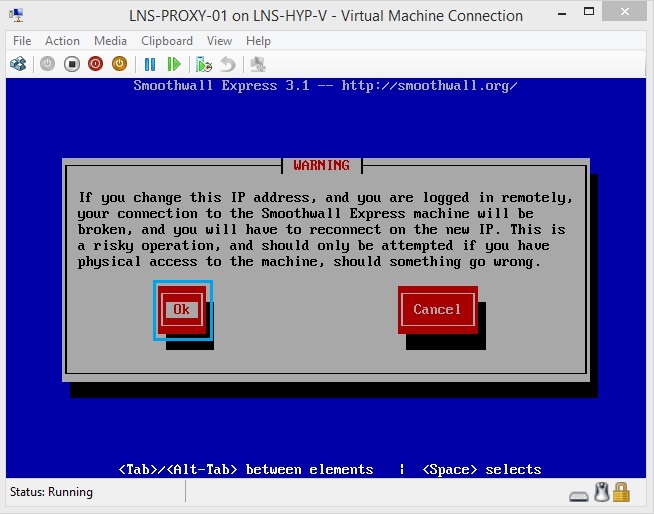
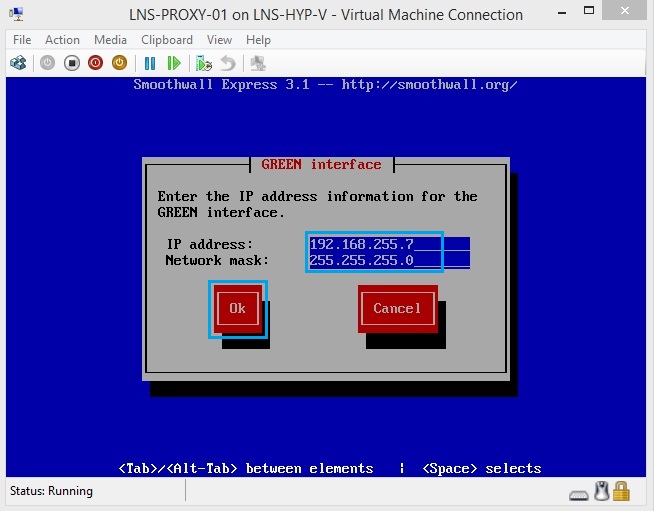
39. Enter the IP Details of the Inside Zone, which in this case is in VLAN 255. I have used 192.168.255.7 /24 as the interface IP.
40. Select “Red” and hit “OK” to specify IP details for the Outside zone.
41. Select “Static” and leave the default “DHCP Hostname”. Allocate an IP on the Outside Interface, in this case i have used 192.168.10.7 /24 which is within VLAN 10. Hit “OK” to exit.
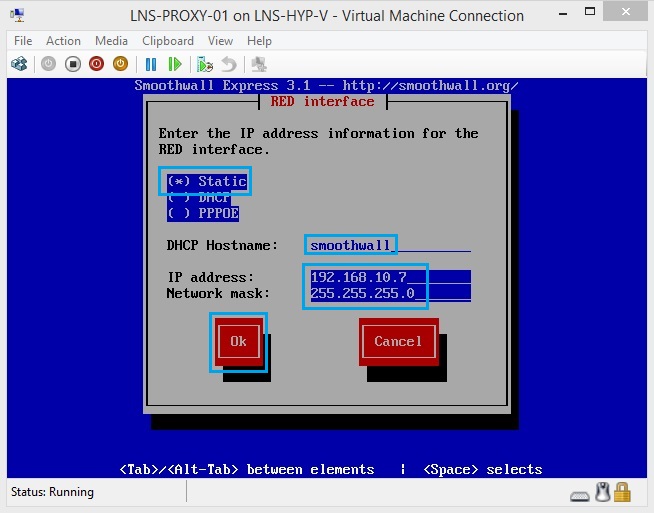
42. Now select “Done” to apply the settings.
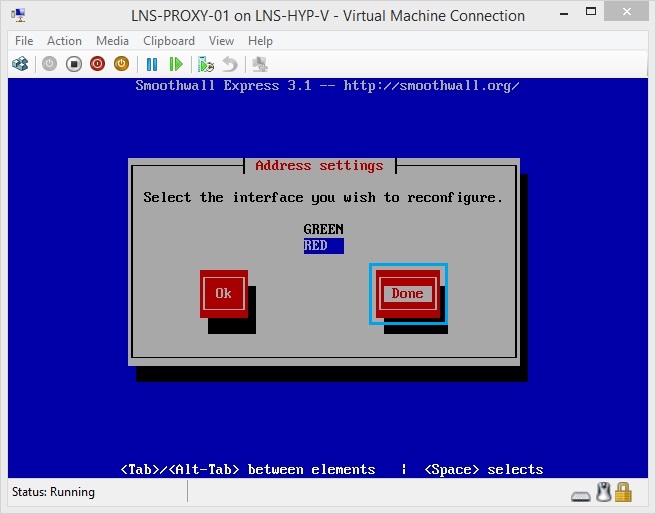
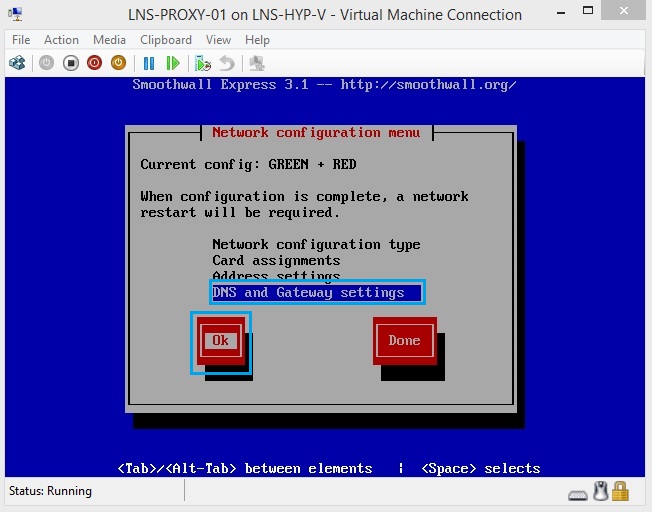
43. Select “DNS and Gateway Settings” and click “OK”
44. Enter the DNS information and the default gateway address the smoothwall device will use to get off the network. In this case our default getaway is on the outside so this is our firewall at 192.168.10.1
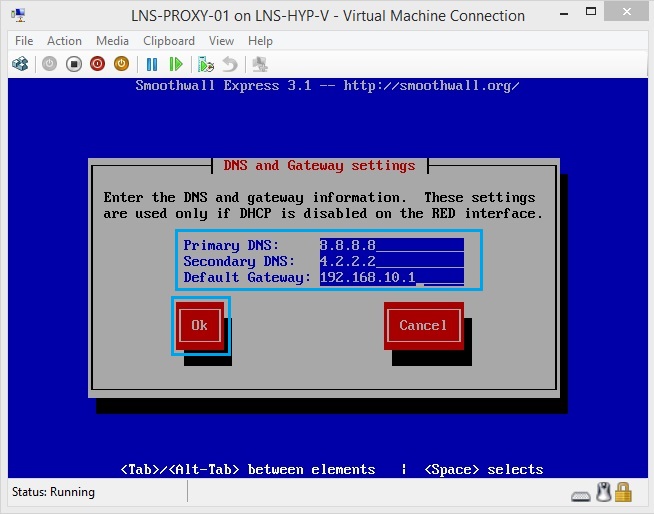
45. Select “Done” to apply the settings
46. Select “Finished” to complete setup
47. Now enter a password for the “admin” user, this is the account that will be used to administer the device via the web GUI. Click “OK”
48. Enter a password for the “root” user, this is the account that will be required to administer the device via CLI using console/SSH
49. Click “OK” the device will reboot.
The “Smoothwall Login” prompt will indicate that the device is now ready
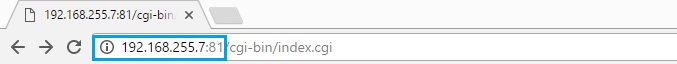
50. Launch a browser and using http, navigate to the address of the smoothwall device on the inside interface on port 81. for eg. “http://192.168.255.7:81”, at the prompt login using the “admin” credentials. (https can also be used on port 441)
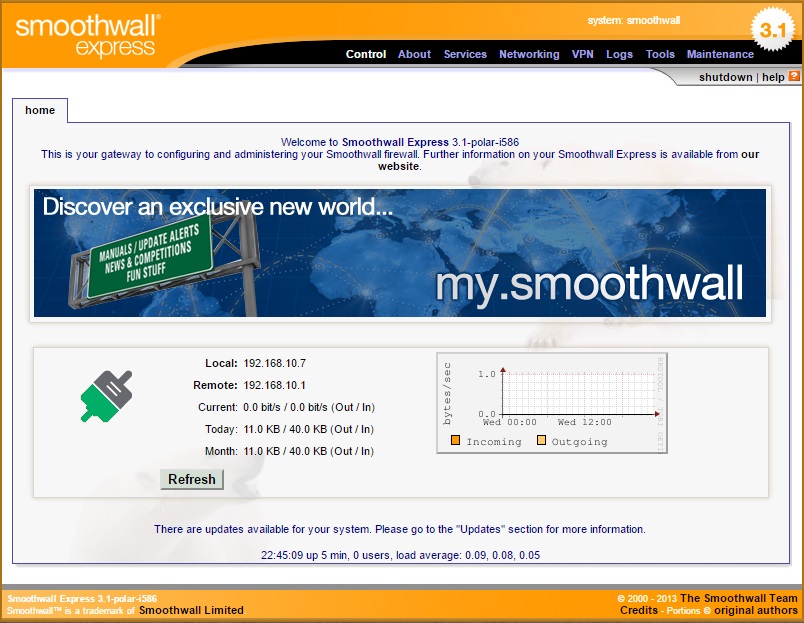
51. After successfully authenticating we should now be able to see the home screen of the GUI interface of the smoothwall device.
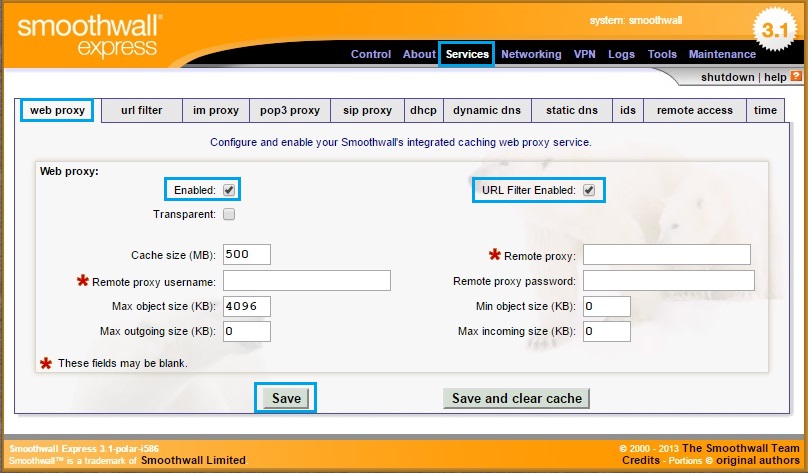
52. By default the Web proxy and URL filtering features are disabled, so this needs to be enabled, to do this – navigate to “Services” – “Web Proxy” and tick “Enabled” and tick “URL Filter Enabled” hit “Save”. We also have the option of enabling the web proxy in “Transparent” mode. however in this example we are deploying the smoothwall as a explicit proxy.
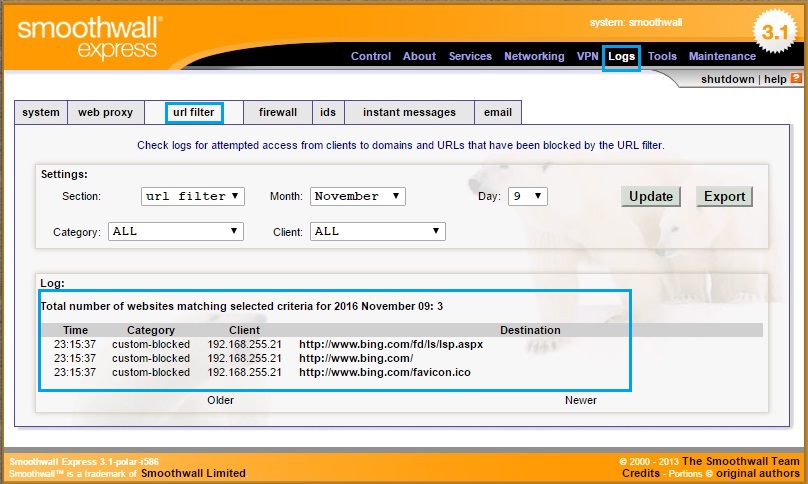
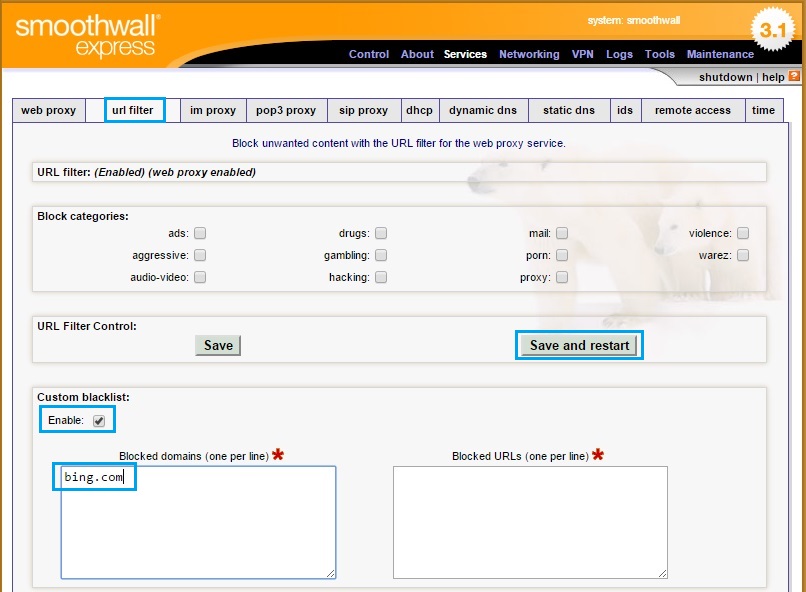
53. Now that the URL filtering features have been enabled lets create a custom blocked list and test the explicit proxy. Click “URL Filter” and under “Custom Blacklist” tick “Enable”. In the “Blocked Domains” field enter a test domain to block. I have used “bing.com” for this example. hit “Save and restart”
57. Launch “DNS” to create a DNS entry for the smoothwall device
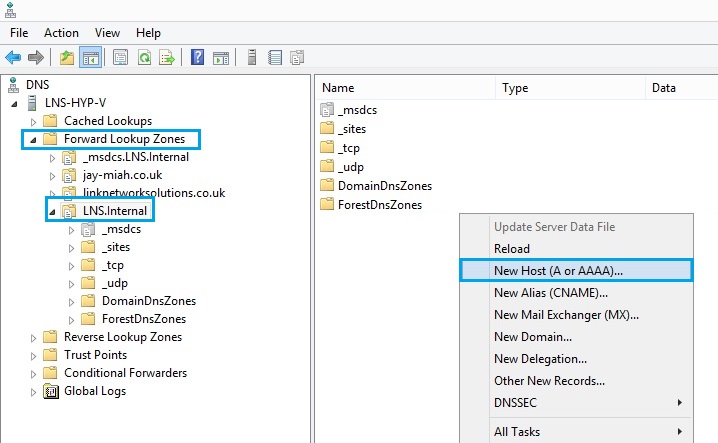
58. From the DNS window expand “Forward Lookup Zones” and within the internal domain zone right click and create a “New Host (A or AAAA)..” record.
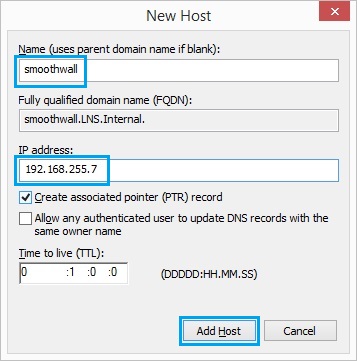
59. Enter the name of the device and its IP address, hit “Add Host”
60. Hit “OK”
The host record should now be visible under the zone.
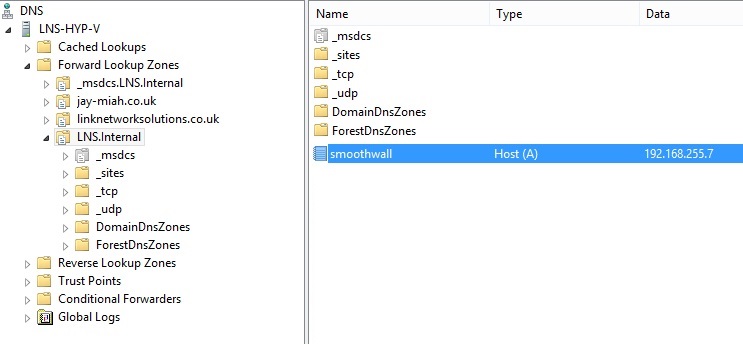
61. Test the new record to verify DNS is able to resolve the hostname of the smoothwall device to the IP address specified, Launch “CMD” and type “nslookup smoothwall”
62. Launch “Internet Options”
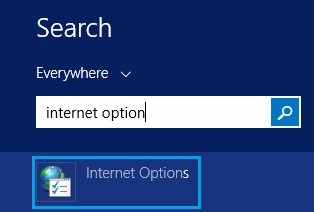
63. Click “Connections” and hit “LAN Settings”
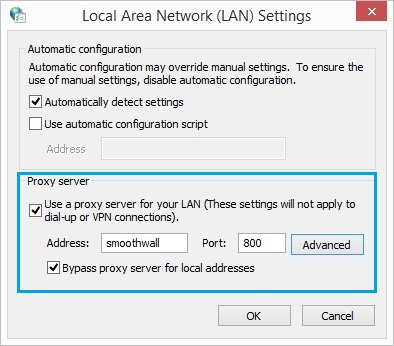
64. Under “Proxy Server” Tick “Use a proxy server for your LAN” and specify the DNS name of the smoothwall device followed by the port no. “800”. Click “OK” and close the Internet options dialog box
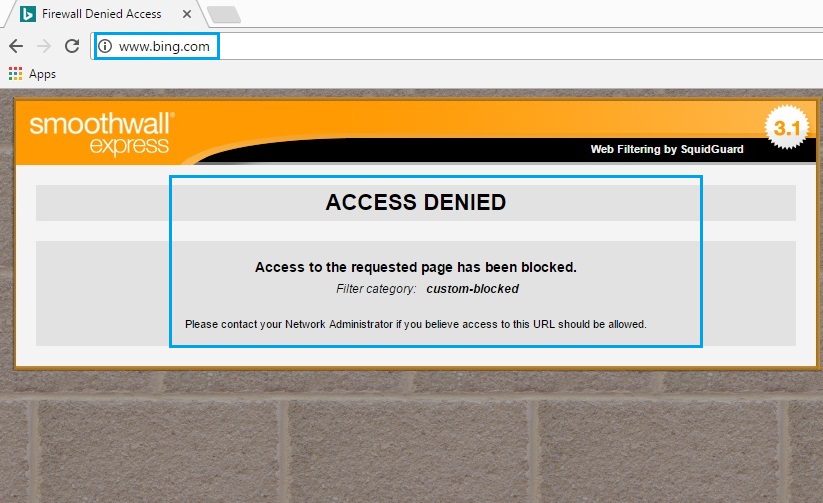
65. Launch a browser and navigate to the previously blocked site and verify if smoothwall blocks the page. In this example we blocked “bing.com” and we can see that a splash page is displayed showing the page is being blocked due to a policy enforcement.
66. Navigate to “Logs” – “URL Filter” and verify there is a log record of the action taken by smoothwall.