Cisco Port-Security Concept/Implementation
Cisco port security is a layer 2 traffic control feature used to protect the network from unknown devices which may be plugged into the network either via a network point in a publicly available space or by a malicious user who has physical access to a network point. Port security works by first setting a limit on the number of MAC addresses a port can learn and then specifying a violation action once the maximum is reached.
Port security is configured the following way:
1. Set the switch port to either “Access” or “Trunk” (Dynamic ports cannot use port security)
2. Set a maximum number of MAC address the port can learn
3. Set the method the port will use to learn the MAC addresses, there are 3 modes we can use:
–Dynamic – Learn source MAC addresses dynamically as the frames enter the switch, and only remember them for the default 5 mins unless another frame enters the switch with the same source MAC in which case renew the timer.
–Static – Statically set MAC addresses that are going to use the port
–Sticky – let the switch learn the source MAC addresses as frames enter the switch however automatically put the MAC addresses into the running-configuration
4. Set a violation action from either of the following four:
–Protect – After the maximum is reached, take no further action when a violation occurs
–Restrict – Same as “Protect” but sends SNMP alerts every time a violation occurs
–Shutdown the port (The default) – once the maximum is reached if a violation occurs, the port is shut down or put into an “err disabled” state, & SNMP alerts sent
–Shutdown the VLAN –once the maximum is reached if a violation occurs, the VLAN is shut down or put into an “err disabled” state& SNMP alerts sent
5. Enable port security on the interface
One of the main reasons for using port security is to mitigate a CAM table overflow attack by setting a limit on how many MAC addresses a port can learn.
A CAM table is the “Content Accessible Memory” of a switch, this is used to store MAC addresses that the switch learns. This information is time stamped and stored for a total of 300 seconds unless it is renewed by a new frame with the same source MAC address entering the switch.
A CAM table overflow attack is when a malicious user sends thousands of frames into the switch each with a different unique source MAC address. This type of attack causes the CAM table to become full, normally a switch has a limit on how many MAC addresses it can store – this is around 5000. As the CAM table becomes full the switch forgets the MAC addresses of the actual devices that are directly connected and ends up forwarding all frames that come into the switch out of all the interfaces. Primarily acting as a Hub.
At this point a malicious user can capture the packets using Wireshark or something similar to gain valuable information.
The other types of attacks that can be mitigated by using port security include:
DHCP Starvation Attack – hundreds of frames with unique source MAC addresses request IP addresses from the real DHCP server thus exhausting out the IP scopes, a malicious user can then bring in a rouge DHCP server to issue IP addresses to users and carry out a “Man in the Middle Attack” (MITM) by making themselves the default gateway and routing traffic for the users. The malicious user would be able to capture all the traffic as it passes through them, and the users would not be aware. By setting a limit on the MAC addresses the switch can prevent the exhaustion on the IP addresses.
Denial of Service (DOS) Attacks – As above, however only exhausting out the DHCP scopes so actual devices are unable to obtain a valid IP address from the DHCP server.
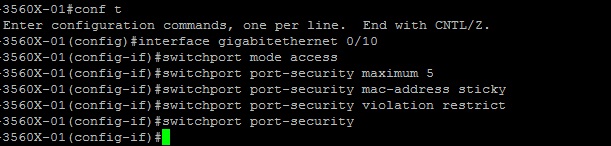
Configuration example:
#conf t – Enter global configuration mode
#interface gigabitethernet 0/10 – Enter the interface configuration mode
#switchport mode access – set the port as an access port
#switchport port-security maximum 5 – set the maximum no. of MAC addresses
#switchport port-security mac-address sticky – Set the method to learn MAC addresses
#switchport port-security violation restrict – set the violation action
#switchport port-security – enable port security
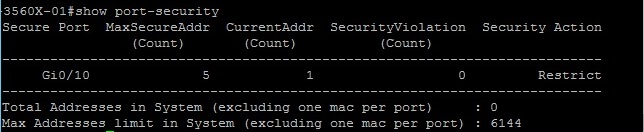
#show port-security – show the configured parameters for port security. We can see that port security is configured and currently there are no violations
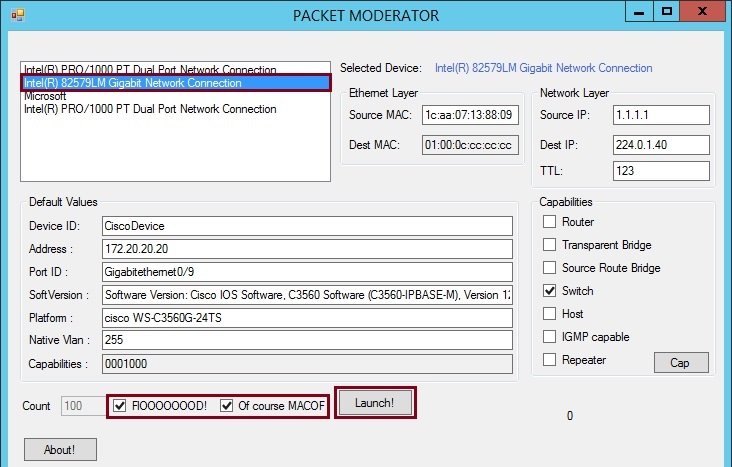
If we now test out port security by flooding the switch port with MAC addresses we can see if port security works correctly. To do this we can use a tools called “Packet Moderator”
Launch the tool, select the correct NIC that is connected to the switch, tick “FlOOOOOOOOD!”, tick “Of course MACOF” and click “Launch”
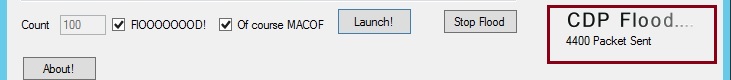
The “packets sent” should shoot up to the thousands, this tool is sending thousands of frames into the switch.
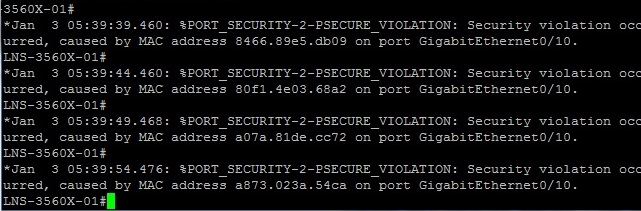
We can see that the switch is reporting the port security violation on the interface we configured port security on.
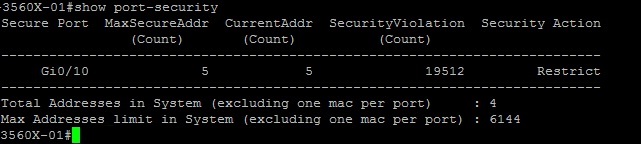
If we have a look at the port security details, we can see that the Maximum is 5, “Current Address Count” is 5 and the “Security Violation Count” is “19512” This information is telling us that port security is doing its job and not allowing more than 5 MAC addresses on the port. It also is telling us that anything above the 5 is being recorded as a violation. Using this table we can identify whether the switch is under attack.
#show port-security
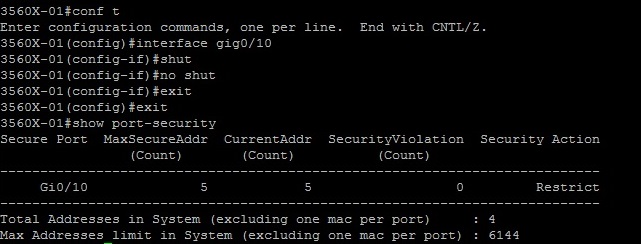
To clear the counters the port needs to be shut down and then brought back up.
#conf t
#int gig0/10
#shutdown
#no shutdown
#exit
#show port-security