Anti-Spoofing on a Checkpoint Firewall
IP Spoofing is a technique of generating IP packets with a source address that belongs to someone else.
Spoofing creates a danger when hosts on the LAN permit access to their resources and services to trusted hosts by checking the source IP of the packets. Using spoofing, an intruder can fake the source address of their packets and make them look like they originated on the trusted hosts.
Anti-spoofing protection is when we create a firewall rule assigned to the external interface of the firewall that examines source addresses of all packets crossing that interface coming from the outside. If the address belongs to the internal network or the firewall itself, the packet is dropped.
Example:
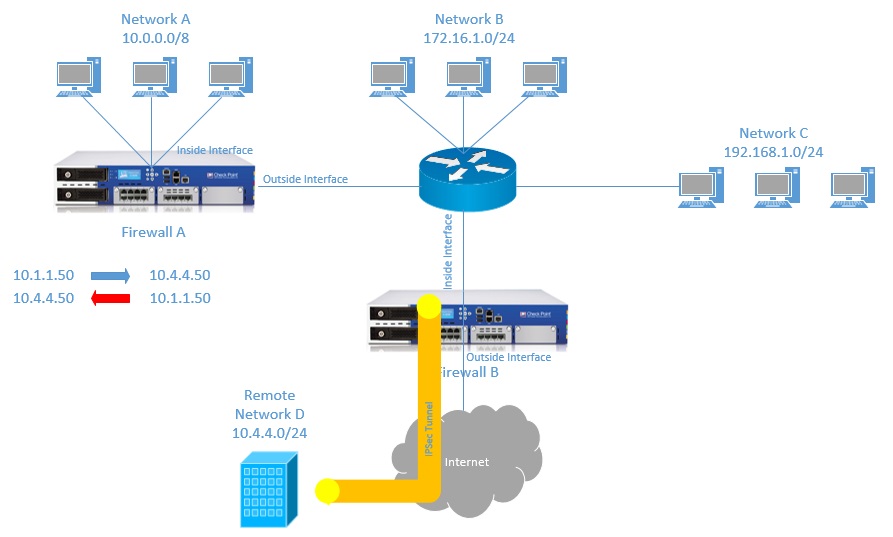
“Network A” uses “10.0.0.0/8” on the internal interface and we have a remote “Network D” that uses “10.4.4.0/24” over the VPN tunnel. If any devices within “Network A” sends packets to “Network D” the forward traffic will flow fine given the correct routing is in place however the firewall will look at the reply traffic and notice that the source of that packet is from the “10” subnet and instantly drop it.
For “Firewall A” the device makes sure that
- All incoming packets to the “Outside Interface” come from “Network B”, “Network C” or “Internet”
- All Incoming packets to the “Inside Interface” come from “Network A”
For “Firewall B” the device makes sure that
- All incoming packets from the “Outside Interface” come from “Internet”
- All incoming packets from the “Inside Interface” come from “Network A”, “Network B” or “Network C”
The firewall already knows that the 10.0.0.0/8 belongs on the internal interface behind “Firewall A” so it suspects the IP address is being spoofed. This behaviour is correct.
Generally you want to ensure that anti-spoofing is used to prevent spoofed IP addresses from being used by an attacker to take advantage of your network.
However in some situations you may need to a allow traffic through without being inspected, commonly this may be in a site-to-site VPN scenario where the 3rd party also uses the same private addressing schema on their encryption domain.
As long you are sure the traffic is coming from a verified source you can create exceptions to exempt the spoofing for that network.
In the steps below we will setup Anti-spoofing on a Checkpoint firewall on the both internal and external interfaces and then create an exception to allow the traffic from the remote network that is using a “10” network on the outside.
Configure Anti-Spoofing on the internal Interface
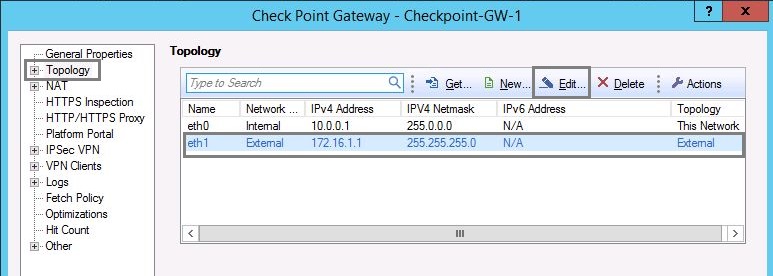
1. In SmartDashboard, from the“Network Objects” tree, double-click the Security Gateway.
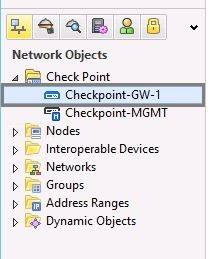
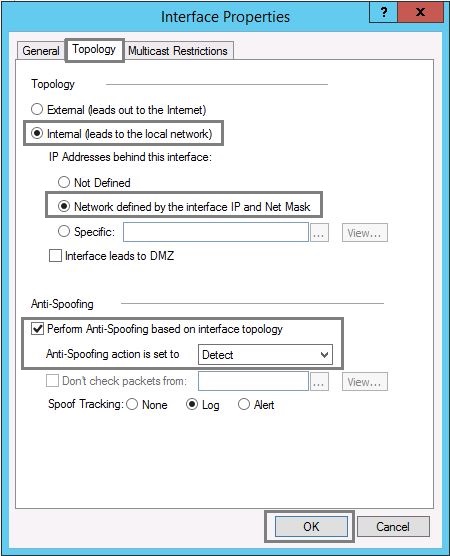
2. From the navigation tree, click “Topology”. Select the “Internal” interface and click “Edit”.
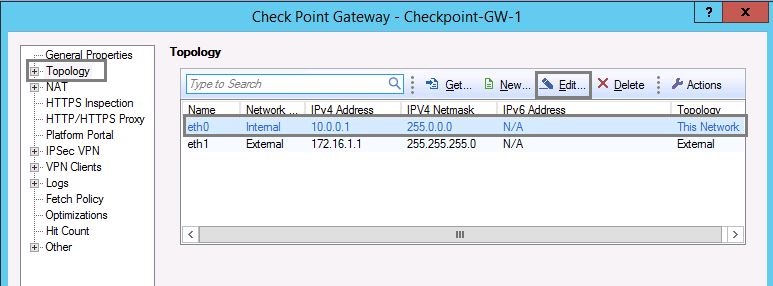
3. Click the “Topology” tab, select “Internal (leads to local Network)”, and Select the option for “Network defined by the interface IP and Net Mask”
Tick “Perform Anti-Spoofing based on interface topology” and Select “Anti-Spoofing action is set to” as either –
Prevent – Drops spoofed packets.
Detect – Allows spoofed packets.
It is recommended using the “Detect” option to monitor traffic. And click “OK”
Configure Anti-Spoofing on the External Interface and exempt a specific network from anti-spoofing inspection.
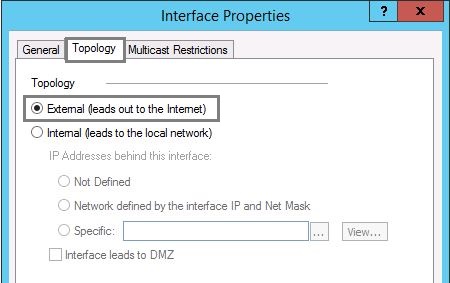
1. From the navigation tree, click “Topology”. Select the “External” interface and click “Edit”.
The “Interface Properties” window opens.
2. Click the “Topology” tab, select “External (leads out to the Internet)”
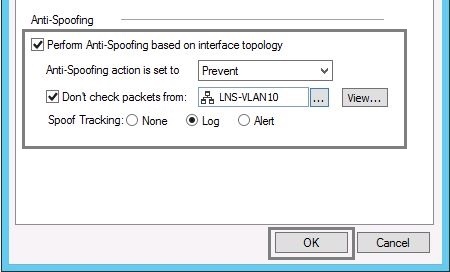
3. Tick “Perform Anti-Spoofing based on interface topology” and Select “Anti-Spoofing action is set to” as
Prevent – Drops spoofed packets.
Tick “Don’t check packets from”.
Click the field, and select the Group or Network object that you are not including in Anti-spoofing. In our case this will be “Network D”
From “Spoof Tracking”, select “Log” and click “OK”
4. Click “OK” and install the policy.